
Error

Error

Error

Subscribed

The request was successfully sent

Error

Message sent

Error
There is "Maxnet" coverage at Your address

The request was successfully sent

No coverage

Error

Feedback sent successfully

Error

Feedback sent successfully

Error

Request sent successfully

Error

CV sent successfully

The request for the domain transfer is successfully sent

Error
02.04.2025
Internet
4552
Have you heard the acronym DDoS more than once? If you still haven't learnt what it is and whether it is dangerous, our today's article will be interesting.
A Distributed Denial of Service attack (DDoS attack) is a set of malicious actions aimed at bringing a computer system to failure. During such a hacker attack, ordinary users are restricted (or unavailable) from accessing a resource. Today, DoS/DDoS attacks are a common practice, as they easily disable most systems, leaving virtually no trace of the attacker.
The first such attacks were launched in the late 90s and have threatened all owners of Internet resources ever since. History knows many attacks that paralyzed even large resources:
However, it is worth noting that DDoS have become less successful as many technical means have been developed to counter the actions of attackers.
How it works
The attack utilizes the limited bandwidth of systems, which is common to all network resources. Hackers use the limitations of the number of incoming requests and the width of the Internet connection channel. The attacked server simultaneously starts receiving a huge number of requests and «goes down».
There is a similar concept of flooding. The difference with DoS is that flooding clogs the channel with a huge amount of unnecessary information, while DoS packets contain deliberately incorrect information so that the server cannot process it.
DoS and DDoS are also easy to distinguish. DoS assumes 1 source of attack, while DDoS assumes 2 or more.
DDoS attack sources are so-called «bots». They are created by infecting machines that have an operating system with viruses (not only computers/phones but also SMART TVs, washing machines, SMART HOME systems, etc.).
What are the purposes of DDOS?
Unfortunately, today it is possible to organize an attack without understanding the mechanics. There are special services that can «choke» almost anyone. An independently organized attack is usually more effective. There may be several reasons for such events:
Current Trends in DDoS
DDoS attacks are constantly evolving. While in the past they were relatively simple and limited to overloading servers, today cybercriminals use more sophisticated and effective methods. For example:
«Complications»
Sometimes a DDoS attack is just the beginning of the problems. While the server is under attack, it is extremely vulnerable, which means that something important can be «pulled» from it. For example, data about your customers, which they leave in feedback forms.
Therefore, be prepared for the fact that attackers will demand money not only for leaving the site alone, but also for not «leaking» important data. Going in contact with hackers and, even more so, paying them, will not be the best idea in any case. Therefore, think through a plan of action in case of such situations, and find out how severe the damage will be in the worst-case scenario. Back up your information and use tools to prevent DDoS attacks.
Countermeasures
Defense against DDoS attacks can be active and passive. Passive measures involve, first of all, the use of special software. It also includes the exclusion of factors that irritate ill-wishers from their activities. Ambiguous method. If your business is successful — you will always have envious people.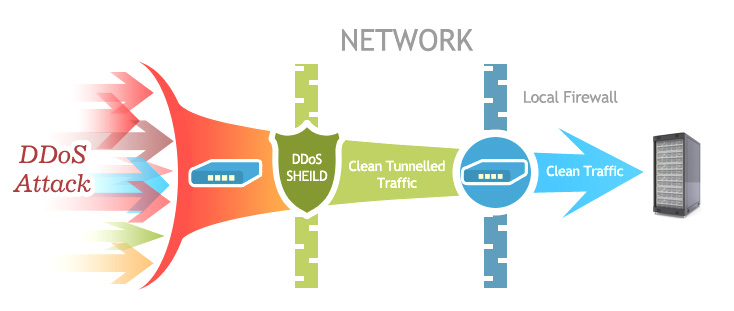
Active includes filtering and blocking network traffic at the backbone provider level. This is done through firewalls and ACL (Access Control List). The latter are responsible for differentiating access to the resource.
If your resource has sufficient server capacity and you have a team of smart specialists, you can not only block hackers' traffic but also redirect it back to them.
Advanced protection methods
Both standard and newer technologies are used to protect against DDoS attacks:Our variant
It is impossible to guarantee complete site security from DDoS. It is possible to take all necessary measures to block traffic and quickly stop the attack in emergency cases. This requires confidence in the technical platform, the absence of system vulnerabilities, and the organization of a monitoring system. Timely notification of danger will solve most problems.
The optimal option is to use the services of proven data centers. Such is the technical platform Maxnet. The range of services of our data center includes hosting and renting virtual servers with protection against DDoS attacks.
Our specialists have not once had to face such actions of intruders, it has become an irreplaceable experience. We clearly understand how to respond to different types of DDoS attacks, and therefore promptly eliminate threats.
To order the services of our Data Centre, contact our managers by mail dc@maxnet.ua or via the feedback form on the website.
Rate
5.0
Share
Comments
0
More comments